Windows Azure AD: 7 Powerful Features You Must Know in 2024
Ever wondered how millions of businesses securely manage user access across cloud apps? The answer often lies in Windows Azure AD—a game-changer in identity and access management. Let’s dive into what makes it so essential today.
What Is Windows Azure AD and Why It Matters

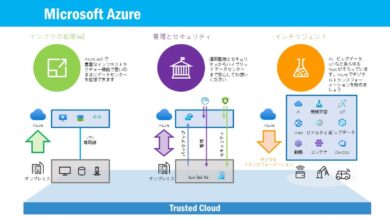
Windows Azure AD, officially known as Microsoft Entra ID (formerly Azure Active Directory), is Microsoft’s cloud-based identity and access management service. It enables organizations to securely sign in and access resources like Microsoft 365, Azure, and thousands of SaaS applications.
Understanding the Core Purpose
At its heart, Windows Azure AD is designed to manage user identities and control access to applications and resources. Unlike traditional on-premises Active Directory, which focuses on managing local network resources, Azure AD is built for the cloud era.
- Centralizes identity management across cloud and on-premises environments.
- Supports single sign-on (SSO) for seamless access to multiple apps.
- Enables secure authentication through multi-factor authentication (MFA).
“Azure AD is not just a directory; it’s the identity backbone of the modern enterprise.” — Microsoft Tech Community
Evolution from On-Premises AD to Cloud Identity
Traditional Active Directory was built for Windows-centric networks where users, devices, and applications lived within the corporate firewall. As businesses moved to the cloud, this model became limiting.
Windows Azure AD emerged as a response to the growing need for cloud-first identity solutions. It supports modern authentication protocols like OAuth 2.0, OpenID Connect, and SAML, making it compatible with a vast ecosystem of cloud applications.
Organizations can now synchronize on-premises directories with Azure AD using Azure AD Connect, enabling hybrid identity models that bridge legacy systems with modern cloud capabilities.
Key Features of Windows Azure AD That Transform Security
One of the biggest reasons for the widespread adoption of Windows Azure AD is its robust feature set. These tools empower IT teams to maintain security without sacrificing user experience.
Single Sign-On (SSO) Across Thousands of Apps
With Windows Azure AD, users can access over 2,600 pre-integrated SaaS applications with a single set of credentials. This includes popular platforms like Salesforce, Dropbox, and ServiceNow.
- Reduces password fatigue and improves productivity.
- Administrators can assign apps to users or groups directly from the Azure portal.
- Supports both cloud and on-premises app integration via Application Proxy.
For example, a marketing team using HubSpot, Zoom, and Google Workspace can log in once and access all tools without re-entering credentials—thanks to SSO powered by Windows Azure AD.
Multi-Factor Authentication (MFA) for Enhanced Security
In an age of rising cyber threats, passwords alone are no longer enough. Windows Azure AD offers built-in MFA that requires users to verify their identity using at least two methods.
- Options include phone calls, text messages, authenticator apps, or biometric verification.
- MFA can be enforced based on risk level, location, or device compliance.
- Available in Azure AD Free, but with limited usage policies in higher tiers.
According to Microsoft, enabling MFA blocks over 99.9% of account compromise attacks. That’s a compelling reason to activate it across your organization.
Conditional Access: Smart Policies for Dynamic Security
Conditional Access is one of the most powerful features in Windows Azure AD. It allows administrators to create policies that enforce access controls based on specific conditions.
- Conditions include user location, device compliance, sign-in risk, and application sensitivity.
- For instance, you can block access from unknown countries or require MFA when accessing financial systems.
- Policies are evaluated in real-time during sign-in attempts.
This dynamic approach ensures that security adapts to context, rather than applying rigid rules across all scenarios.
Windows Azure AD vs Traditional Active Directory: Key Differences
While both systems manage identities, Windows Azure AD and on-premises Active Directory serve different purposes and architectures. Understanding these differences is crucial for modern IT planning.
Architecture and Deployment Model
Traditional Active Directory runs on Windows Server and requires domain controllers within a local network. It uses LDAP, Kerberos, and NTLM for authentication.
In contrast, Windows Azure AD is a cloud-native service. It doesn’t rely on domain controllers and uses REST APIs and modern authentication protocols. This makes it inherently more scalable and resilient.
- AD: On-premises, server-dependent, requires maintenance.
- Azure AD: Cloud-hosted, globally available, automatically updated.
User and Resource Management
On-premises AD excels at managing Windows devices, file servers, and internal applications. It supports Group Policy Objects (GPOs) for centralized configuration.
Windows Azure AD, however, is optimized for managing user access to cloud resources. It supports device registration (not domain joining) and integrates with Microsoft Intune for mobile device management.
- AD: Manages domain-joined devices and local resources.
- Azure AD: Manages cloud identities and hybrid access.
Authentication Protocols and Integration
Traditional AD relies heavily on legacy protocols like NTLM, which are less secure and not suitable for the internet. Azure AD, on the other hand, uses modern standards like OAuth 2.0 and OpenID Connect.
This shift enables secure federation with external partners and seamless integration with web and mobile apps. For example, a developer building a React app can use Azure AD for authentication via OpenID Connect without needing backend LDAP servers.
Learn more about protocol differences at Microsoft’s official documentation.
How Windows Azure AD Powers Hybrid Identity Solutions
Many organizations aren’t ready to go fully cloud-only. That’s where hybrid identity comes in—combining the best of on-premises AD and Windows Azure AD.
Using Azure AD Connect for Synchronization
Azure AD Connect is the bridge between on-premises Active Directory and Windows Azure AD. It synchronizes user accounts, groups, and passwords from local directories to the cloud.
- Supports password hash synchronization, pass-through authentication, and federation.
- Allows users to use the same password for both on-prem and cloud resources.
- Can be configured for filtering—sync only specific OUs or attributes.
This tool is essential for organizations transitioning to the cloud while maintaining existing infrastructure.
Password Hash Sync vs Pass-Through Authentication
When setting up hybrid identity, administrators must choose how authentication is handled. Two common methods are Password Hash Sync (PHS) and Pass-Through Authentication (PTA).
- Password Hash Sync: Hashes of user passwords are synced to Azure AD. Authentication happens in the cloud.
- Pass-Through Authentication: On-prem agents validate the password in real-time without storing it in the cloud.
PTA is considered more secure because passwords never leave the on-prem environment. However, PHS is simpler to deploy and requires fewer on-prem components.
Seamless Single Sign-On (SSO)
Windows Azure AD offers Seamless SSO, which allows users on domain-joined devices to automatically sign in to cloud apps without re-entering credentials.
- Works when the device is connected to the corporate network or via VPN.
- Leverages Kerberos decryption keys stored in Azure AD.
- Improves user experience while maintaining security.
This feature is especially useful for large enterprises with a mix of cloud and on-prem apps.
Security and Compliance with Windows Azure AD
In today’s regulatory landscape, security and compliance are non-negotiable. Windows Azure AD provides tools that help organizations meet industry standards and protect sensitive data.
Identity Protection and Risk-Based Policies
Azure AD Identity Protection uses machine learning to detect suspicious sign-in behaviors and risky user activities.
- Identifies anomalies like sign-ins from unfamiliar locations or anonymous IP addresses.
- Assigns risk levels (low, medium, high) to sign-ins and users.
- Can automatically enforce actions like blocking access or requiring password resets.
These insights are integrated with Conditional Access, allowing automated responses to threats.
Privileged Identity Management (PIM)
Not all users should have permanent admin rights. Windows Azure AD’s Privileged Identity Management (PIM) enables just-in-time (JIT) access for administrators.
- Admin roles are inactive until activated.
- Activation requires approval, MFA, and justification.
- Access can be time-limited (e.g., 4 hours).
PIM reduces the attack surface by minimizing standing privileges. It’s available in Azure AD Premium P2 and integrates with Azure RBAC.
Compliance and Audit Logging
Windows Azure AD provides comprehensive audit logs that track user sign-ins, administrative changes, and policy updates.
- Logs can be exported to SIEM tools like Splunk or Microsoft Sentinel.
- Supports compliance with GDPR, HIPAA, ISO 27001, and other standards.
- Includes anomaly detection and reporting dashboards.
Regular audits help organizations detect misuse, investigate incidents, and demonstrate compliance during audits.
Windows Azure AD Licensing Tiers Explained
Windows Azure AD comes in four licensing tiers: Free, Office 365 Apps, Premium P1, and Premium P2. Each offers increasing levels of functionality.
Azure AD Free Edition
The Free edition is included with any Microsoft cloud subscription, such as Microsoft 365 or Azure.
- Basic user and group management.
- Support for 500,000 objects (users, groups, contacts).
- Limited SSO and MFA (MFA available but not policy-based).
Suitable for small businesses or departments testing cloud identity.
Azure AD Premium P1
Premium P1 adds advanced features for access management and security.
- Conditional Access policies.
- Self-service password reset (SSPR) for cloud and on-prem users.
- Group-based access management and dynamic groups.
- Hybrid identity with Azure AD Connect.
Ideal for mid-sized organizations needing policy-driven access control.
Azure AD Premium P2
Premium P2 includes all P1 features plus advanced security tools.
- Privileged Identity Management (PIM).
- Identity Protection with risk detection and automated responses.
- Advanced reporting and analytics.
Best suited for enterprises with strict security and compliance requirements.
Best Practices for Deploying Windows Azure AD
Deploying Windows Azure AD successfully requires careful planning and execution. Follow these best practices to ensure a smooth transition.
Start with a Clear Identity Strategy
Before deploying, define your identity model: cloud-only, hybrid, or on-premises with cloud sync. Assess your current AD structure and plan how users and groups will be migrated or synchronized.
- Identify critical applications and their authentication needs.
- Plan for naming conventions and group structures in Azure AD.
- Engage stakeholders from IT, security, and business units.
Implement Multi-Factor Authentication Early
MFA should not be an afterthought. Enable it early in the deployment process to protect administrative accounts and high-risk users.
- Start with admins, then expand to all users.
- Use Conditional Access to enforce MFA for sensitive apps.
- Educate users on MFA methods and troubleshooting.
Use Conditional Access to Enforce Security Policies
Instead of blanket rules, use Conditional Access to apply security contextually.
- Block legacy authentication protocols (e.g., IMAP, SMTP).
- Require compliant devices for accessing corporate data.
- Monitor policy impact using the What-If tool in the Azure portal.
For detailed guidance, visit Microsoft’s Conditional Access documentation.
Future Trends: Where Is Windows Azure AD Heading?
As digital transformation accelerates, Windows Azure AD continues to evolve. Microsoft is investing heavily in identity security, zero trust, and AI-driven protection.
Zero Trust Adoption and Identity-Centric Security
The Zero Trust model—“never trust, always verify”—is becoming the standard for enterprise security. Windows Azure AD is at the core of Microsoft’s Zero Trust framework.
- Every access request is authenticated, authorized, and encrypted.
- Device health and user behavior are continuously assessed.
- Integration with Microsoft Defender for Cloud Apps enhances visibility.
Organizations are shifting from perimeter-based security to identity-first approaches, with Azure AD as the foundation.
AI-Powered Threat Detection
Microsoft is leveraging AI and machine learning to improve threat detection in Windows Azure AD.
- Anomalous sign-in patterns are detected in real-time.
- Risk policies can be auto-adjusted based on historical behavior.
- Automated investigations reduce response time to incidents.
These advancements make Azure AD not just a directory, but an intelligent security layer.
Integration with Microsoft Entra Suite
In 2023, Microsoft rebranded Azure AD as Microsoft Entra ID, part of the broader Entra suite focused on identity and access.
- Entra ID: Core identity platform (formerly Azure AD).
- Entra Permissions Management: For managing permissions across multi-cloud environments.
- Entra Workload Identities: For non-human identities like apps and services.
This evolution reflects Microsoft’s vision of a unified, intelligent identity fabric across cloud and on-premises systems.
What is Windows Azure AD?
Windows Azure AD, now known as Microsoft Entra ID, is a cloud-based identity and access management service that enables secure user authentication and resource access across Microsoft 365, Azure, and thousands of SaaS applications.
How does Windows Azure AD differ from on-premises Active Directory?
While traditional Active Directory manages on-premises resources using LDAP and domain controllers, Windows Azure AD is cloud-native, uses modern protocols like OAuth, and focuses on securing access to cloud applications and services.
Is Multi-Factor Authentication free in Windows Azure AD?
Yes, MFA is available in all Azure AD editions, including the Free tier. However, policy-based control and per-user MFA settings require Azure AD Premium licenses.
Can I use Windows Azure AD for on-premises applications?
Yes, using Azure AD Application Proxy, you can publish on-premises web applications securely to the cloud and enable remote access with SSO and MFA.
What is the cost of Azure AD Premium P1 and P2?
As of 2024, Azure AD Premium P1 costs approximately $6/user/month, and Premium P2 is around $9/user/month. Pricing may vary based on subscription type and volume.
Windows Azure AD has evolved from a simple cloud directory into a comprehensive identity and security platform. Whether you’re managing a small team or a global enterprise, its features—from SSO and MFA to Conditional Access and Identity Protection—provide the tools needed to secure access in a digital world. As Microsoft continues to innovate with AI, Zero Trust, and the Entra suite, the future of identity management is smarter and more secure than ever. Now is the time to leverage Windows Azure AD to protect your organization’s digital frontier.
Recommended for you 👇
Further Reading: