Azure Log In: 7 Ultimate Tips for a Secure & Fast Access
Logging into Azure doesn’t have to be complicated. Whether you’re a developer, admin, or new user, mastering the azure log in process is your first step toward seamless cloud management. Let’s break it down—simply, securely, and smartly.
Understanding Azure Log In: The Foundation of Cloud Access

The azure log in process is your gateway to Microsoft’s powerful cloud ecosystem. From managing virtual machines to deploying AI models, everything starts with a secure login. But it’s not just about typing a username and password—it’s about identity, access control, and security protocols working behind the scenes.
What Is Azure Log In?
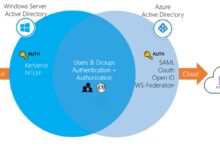
Azure log in refers to the authentication process that verifies your identity before granting access to Microsoft Azure resources. This can include the Azure portal, Azure CLI, PowerShell, or third-party applications integrated with Azure Active Directory (Azure AD). It’s the digital key that unlocks your cloud environment.
Unlike traditional login systems, Azure uses modern identity frameworks such as OAuth 2.0, OpenID Connect, and SAML 2.0 to ensure secure and scalable access. This means your credentials are validated through Microsoft’s identity platform, which supports multi-factor authentication (MFA), conditional access, and single sign-on (SSO).
Why Azure Log In Matters for Security
Every azure log in attempt is a potential entry point for threats. Weak passwords, unsecured devices, or phishing attacks can compromise your entire cloud infrastructure. That’s why Microsoft emphasizes Zero Trust security—never trust, always verify.
- Each login is analyzed for risk using signals like location, device health, and sign-in behavior.
- Azure AD Identity Protection can flag suspicious logins and enforce step-up authentication.
- Administrators can set policies to block logins from high-risk countries or unmanaged devices.
“The majority of data breaches start with compromised credentials. Securing the azure log in process is the first line of defense.” — Microsoft Security Report 2023
Step-by-Step Guide to Azure Log In for Beginners
If you’re new to Azure, the login process might seem overwhelming. But with the right guidance, you can access your dashboard in minutes. This section walks you through the essential steps, common pitfalls, and best practices for a smooth azure log in experience.
How to Perform a Basic Azure Log In
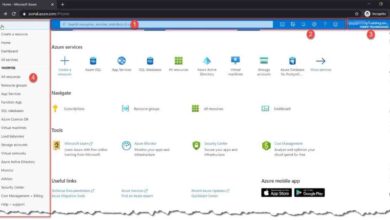
1. Open your browser and go to https://portal.azure.com.
2. Enter your email address (typically your organizational account or Microsoft account).
3. Click ‘Next’ and input your password.
4. If enabled, complete multi-factor authentication (MFA) using an authenticator app, SMS, or phone call.
5. Once verified, you’ll be redirected to the Azure dashboard.
For personal Microsoft accounts (like outlook.com), you may need to switch directories if you’re accessing a work or school subscription. This is common when managing multiple Azure environments.
Troubleshooting Common Azure Log In Issues
Even experienced users face login problems. Here are the most frequent issues and how to resolve them:
- “User not found” error: Ensure you’re using the correct email associated with your Azure subscription. Check for typos or outdated accounts.
- Password reset required: Use the ‘Forgot password?’ link to reset via email or phone. Admins can also reset passwords in Azure AD.
- MFA not working: If your authenticator app isn’t generating codes, re-sync the time or re-register the device.
- Stuck on loading screen: Clear browser cache, disable extensions, or try an incognito window.
For persistent issues, visit the Azure Status Page to check for service outages.
Azure Log In Methods: Beyond Username and Password
Modern cloud environments demand more than just passwords. Azure supports multiple authentication methods to enhance security and usability. Understanding these options helps you choose the best azure log in method for your needs.
Using Microsoft Authenticator App
The Microsoft Authenticator app is one of the most secure ways to perform an azure log in. It supports push notifications, time-based one-time passwords (TOTP), and passwordless sign-in.
To set it up:
1. Go to My Security Info in your Microsoft account.
2. Add the Microsoft Authenticator app.
3. Scan the QR code and approve a test notification.
4. Enable ‘Passwordless sign-in’ for a seamless experience.
Once configured, you’ll receive a push notification during login—just approve it, and you’re in. No typing required.
Biometric and Windows Hello Login
If you’re using a Windows 10 or 11 device, Windows Hello allows you to log in to Azure using facial recognition, fingerprint, or a PIN. This method is both fast and secure because it ties authentication to your device’s Trusted Platform Module (TPM).
Benefits include:
– No password exposure to phishing.
– Faster login than typing credentials.
– Compliant with FIDO2 standards for passwordless authentication.
Administrators can enforce Windows Hello for Business policies through Azure AD to ensure enterprise-grade security.
Single Sign-On (SSO) and Azure Log In Integration
For organizations managing dozens of apps, requiring separate logins for each is inefficient and risky. Azure’s Single Sign-On (SSO) capability allows users to log in once and access multiple applications without re-authenticating—making the azure log in process both convenient and secure.
How Azure SSO Works
Azure AD acts as an identity provider (IdP) that brokers authentication between users and applications. When you perform an azure log in with SSO enabled:
- You authenticate once with Azure AD.
- Azure issues a security token (SAML or OAuth) to the requested app.
- The app trusts Azure’s token and grants access without asking for credentials again.
This is especially useful for SaaS apps like Salesforce, Dropbox, or Office 365, which can be integrated directly into Azure AD.
Setting Up SSO for Enterprise Applications
To configure SSO for an app in Azure:
- Sign in to the Azure portal as an administrator.
- Navigate to Azure Active Directory > Enterprise Applications.
- Select the app you want to configure.
- Go to ‘Single sign-on’ and choose the method (SAML, Password-based, or OIDC).
- Follow the setup wizard to upload certificates or configure URLs.
Once set up, users can access the app directly from their MyApps portal (https://myapps.microsoft.com) after a single azure log in.
“SSO reduces password fatigue and decreases the risk of weak or reused passwords.” — Gartner Identity & Access Management Report
Multi-Factor Authentication (MFA) in Azure Log In
Even the strongest password can be compromised. That’s why Multi-Factor Authentication (MFA) is a critical layer in the azure log in process. MFA requires users to verify their identity using two or more factors: something you know (password), something you have (phone), or something you are (biometrics).
Enabling MFA for Users
As an admin, you can enforce MFA for all users or specific groups:
- Log in to the Azure portal.
- Go to Azure AD > Security > Multi-Factor Authentication.
- Select users and click ‘Enable’.
- Notify users to set up their second factor via the MFA setup page.
Users can choose from:
– Microsoft Authenticator app (recommended)
– SMS verification
– Phone call
– Hardware tokens (FIDO2)
Once enabled, every azure log in will require MFA, significantly reducing the risk of unauthorized access.
Conditional Access Policies with MFA
Azure goes beyond basic MFA with Conditional Access—a policy engine that applies access controls based on context. For example, you can require MFA only when:
- Logging in from an untrusted location.
- Accessing sensitive data like financial systems.
- Using a personal device instead of a managed one.
To create a Conditional Access policy:
1. Go to Azure AD > Security > Conditional Access.
2. Click ‘New policy’.
3. Define conditions (user, device, location, app).
4. Set access controls to ‘Require multi-factor authentication’.
5. Enable and test the policy.
This granular control ensures security without sacrificing user experience.
Azure Log In for Developers: CLI, SDKs, and Service Principals
Developers often need programmatic access to Azure resources. The azure log in process for automation differs from human login—it uses service principals, managed identities, or CLI tokens instead of interactive credentials.
Using Azure CLI for Login
The Azure Command-Line Interface (CLI) allows developers to manage resources via scripts. To log in:
az login
This opens a browser window for authentication. Once logged in, the CLI stores an access token for 1 hour.
For non-interactive scenarios (like CI/CD pipelines), use a service principal:
az login --service-principal -u <app-id> -p <password> --tenant <tenant-id>
Ensure the service principal has the necessary role assignments (e.g., Contributor) on the target resources.
Managed Identities for Secure Automation
Instead of storing credentials in code, Azure offers Managed Identities—automatically managed identities for Azure services. When enabled on a VM or App Service, the service can authenticate to other Azure resources (like Key Vault or Storage) without any secrets.
Steps to use managed identity:
1. Enable system-assigned identity on your resource.
2. Grant it permissions via Azure RBAC.
3. Use the identity in your application code to fetch tokens from the IMDS endpoint.
This eliminates credential management and reduces the attack surface during automated azure log in processes.
Security Best Practices for Azure Log In
Every azure log in is a potential security event. Following best practices ensures that your access remains secure, compliant, and resilient against attacks.
Enforce Strong Password Policies
While passwords are becoming less central, they’re still part of the login chain. Azure AD supports custom password policies, including:
- Blocking common weak passwords (e.g., ‘Password123’).
- Enforcing complexity and length.
- Screening against known breached passwords.
Combine this with regular password rotation (if required by compliance) and user education on phishing risks.
Monitor Sign-In Logs and Anomalies
Azure AD provides detailed sign-in logs under Monitoring > Sign-in logs. You can filter by:
- User
- Application
- Sign-in status (success/failure)
- IP address and location
Look for:
– Multiple failed logins (possible brute force)
– Logins from unusual countries
– Anonymous IP addresses (TOR, proxies)
Set up alerts using Azure Monitor or Microsoft Sentinel to detect and respond to suspicious activity in real time.
Implement Just-In-Time (JIT) Access
Instead of granting permanent admin rights, use Privileged Identity Management (PIM) to enable Just-In-Time access. Admins must request elevated privileges, which are granted for a limited time.
This reduces the window of exposure and ensures that even powerful azure log in sessions are time-bound and auditable.
What is the easiest way to log in to Azure?
The easiest way is using a Microsoft account or work/school email with the Azure portal at https://portal.azure.com. If MFA is set up, use the Microsoft Authenticator app for one-tap approval.
Why can’t I log in to my Azure account?
Common reasons include incorrect credentials, expired passwords, MFA issues, or account lockout. Check your internet connection, clear browser cache, or visit the Microsoft Account Recovery page to reset your password.
How do I enable MFA for Azure log in?
Go to the Azure portal, navigate to Azure AD > Security > Multi-Factor Authentication, select users, and click ‘Enable’. Users will be prompted to set up their second factor on next login.
Can I log in to Azure without a password?
Yes. Azure supports passwordless authentication using the Microsoft Authenticator app, Windows Hello, FIDO2 security keys, or SMS one-time codes. Enable these under ‘Security Info’ in your Microsoft account.
What should I do if my Azure account is compromised?
Immediately sign out all sessions, reset your password, revoke app permissions, and check sign-in logs for unauthorized access. Contact Microsoft Support if needed and enable MFA if not already active.
Mastering the azure log in process is essential for anyone using Microsoft’s cloud platform. From basic portal access to advanced developer workflows, every login should be secure, efficient, and aligned with best practices. By leveraging MFA, SSO, conditional access, and modern authentication methods, you can protect your environment while simplifying access. Whether you’re an admin, developer, or end-user, understanding the full scope of azure log in options empowers you to work smarter and safer in the cloud.
Further Reading: