Azure Log In: 7 Powerful Steps to Master Secure Access Now
Logging into Azure doesn’t have to be complicated. Whether you’re a developer, admin, or business user, mastering the azure log in process is your first step toward unlocking Microsoft’s cloud power—safely and efficiently.
Azure Log In: Understanding the Basics

The azure log in process is the gateway to Microsoft Azure, one of the world’s most powerful cloud computing platforms. Millions of users access Azure daily for virtual machines, storage, AI tools, and enterprise applications. But before you can deploy a server or analyze data, you need to securely log in.
What Is Azure Log In?
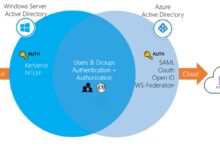
Azure log in refers to the authentication process that verifies your identity when accessing the Azure portal, Azure CLI, Azure PowerShell, or any Azure-integrated service. It ensures only authorized users can manage resources, configure networks, or deploy applications.
This process typically involves a Microsoft account (MSA), a work or school account (Azure Active Directory), or federated identity via third-party identity providers. The login experience varies slightly depending on your account type and security configuration.
- Personal Microsoft accounts (e.g., @outlook.com, @hotmail.com)
- Work or school accounts managed by Azure Active Directory (Azure AD)
- Federated identities using SAML or OAuth 2.0
Understanding which account type you’re using is crucial because it affects how you authenticate, reset passwords, and manage multi-factor authentication (MFA).
Why Secure Azure Log In Matters
In today’s threat landscape, a compromised azure log in can lead to data breaches, unauthorized resource deployment, or even cryptojacking. According to Microsoft’s 2023 Digital Defense Report, over 50 million password spray attacks are blocked monthly across Azure services.
“Every login is a potential entry point. Securing Azure access isn’t optional—it’s foundational.” — Microsoft Security Team
Organizations that fail to enforce strong authentication during the azure log in process risk exposure to phishing, credential stuffing, and insider threats. Implementing identity governance and conditional access policies starts with a secure login.
Step-by-Step Guide to Azure Log In
Successfully logging into Azure requires the right credentials, browser, and awareness of potential issues. Follow this comprehensive guide to ensure a smooth azure log in experience every time.
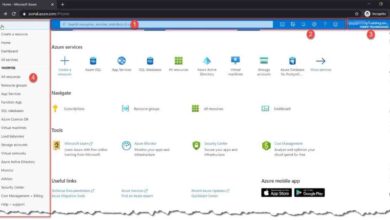
Step 1: Navigate to the Azure Portal
Open your preferred browser and go to https://portal.azure.com. This is the official entry point for the Azure management portal. Avoid third-party links or phishing sites that mimic the login page.
Ensure the URL is correct and the connection is secure (HTTPS with a padlock icon). Microsoft does not host Azure logins on alternative domains like .net or .org for public access.
- Use modern browsers: Chrome, Edge, Firefox, or Safari
- Clear cache if login issues persist
- Disable aggressive ad-blockers that may interfere with authentication flows
Step 2: Enter Your Credentials
Type your email address or phone number associated with your Microsoft or Azure AD account. Click “Next” and enter your password. If you’re using a work or school account, you might be redirected to your organization’s login page.
Some organizations use custom domains (e.g., user@company.com), and their login may include branding, MFA prompts, or conditional access checks before reaching the Azure dashboard.
- Double-check spelling and domain (e.g., @gmail.com vs @outlook.com)
- Use saved credentials only on trusted devices
- Never save passwords on public computers
Step 3: Complete Multi-Factor Authentication (MFA)
After entering your password, you’ll likely be prompted for a second verification method. This is part of Azure’s defense-in-depth strategy. Common MFA options include:
- Microsoft Authenticator app notifications or codes
- Text message (SMS) codes
- Phone calls
- Hardware security keys (FIDO2)
- Biometric verification on trusted devices
Microsoft reports that enabling MFA blocks over 99.9% of account compromise attacks. If you haven’t set up MFA, consider doing so immediately after your first azure log in.
Common Azure Log In Issues and Fixes
Even experienced users encounter problems during the azure log in process. From forgotten passwords to MFA failures, knowing how to troubleshoot is essential.
Forgot Password or Locked Account
If you see messages like “Your account has been locked” or “Incorrect password,” don’t panic. Azure AD automatically locks accounts after multiple failed attempts to prevent brute-force attacks.
Click “Forgot password” on the login screen to begin recovery. You’ll need access to a registered email, phone, or authenticator app. If self-service password reset (SSPR) is enabled by your admin, you can regain access in minutes.
- Ensure your recovery options are up to date
- Contact your IT administrator if SSPR isn’t enabled
- Wait 15–30 minutes for lockout to expire (default policy)
MFA Not Working or Not Receiving Codes
One of the most frequent azure log in issues is MFA failure. Users report not receiving SMS codes, missing push notifications, or outdated authenticator app tokens.
First, check your device’s internet connection. If using the Microsoft Authenticator app, ensure time sync is enabled. For SMS issues, verify your phone number is correct in your profile.
“Time-based one-time passwords (TOTP) rely on accurate clocks. Even a 2-minute drift can cause login failures.” — Azure Identity Support
If you’re locked out, use backup methods like app passwords, alternate MFA options, or contact your administrator for emergency access resets.
Browser or Cache-Related Errors
Sometimes, the problem isn’t with your credentials but with your browser. Cached sessions, outdated cookies, or disabled JavaScript can break the azure log in flow.
Try these steps:
- Clear browsing data (cookies, cache, site data)
- Try an incognito or private browsing window
- Disable browser extensions temporarily
- Update your browser to the latest version
If the issue persists, try a different browser or device to isolate the problem.
Azure Log In for Administrators: Best Practices
For IT administrators, managing azure log in isn’t just about personal access—it’s about securing an entire organization’s cloud footprint. Implementing best practices reduces risk and improves user experience.
Enforce Multi-Factor Authentication
Admins should mandate MFA for all users, especially those with elevated privileges. Use Azure AD Conditional Access policies to require MFA based on user role, location, or device compliance.
Go beyond basic enforcement: configure MFA registration at first sign-in to ensure all users are protected from day one.
- Create a Conditional Access policy requiring MFA for all users
- Exclude break-glass emergency accounts (but protect them with other controls)
- Use trusted locations to reduce MFA prompts for office networks
Learn more about setting up MFA at Microsoft’s official MFA guide.
Implement Conditional Access Policies
Conditional Access is a core feature of Azure AD that allows admins to control access based on real-time signals like user location, device health, and sign-in risk.
For example, you can block logins from high-risk countries, require compliant devices, or force MFA when accessing sensitive apps.
- Block legacy authentication protocols (e.g., IMAP, SMTP)
- Require hybrid Azure AD-joined devices for on-premises access
- Use sign-in risk detection to prompt step-up authentication
These policies are applied during the azure log in process, making them a proactive defense layer.
Monitor Sign-In Logs and Alerts
Azure AD provides detailed sign-in logs in the Azure portal under “Monitoring” > “Sign-ins.” These logs show successful and failed attempts, IP addresses, user agents, and applied policies.
Regularly review logs for anomalies like:
- Logins from unfamiliar countries
- Multiple failed attempts followed by success
- Access during unusual hours
Set up Azure Monitor alerts or use Microsoft Defender for Cloud to get notified of suspicious activity automatically.
Using Azure CLI and PowerShell: Log In via Command Line
For developers and DevOps engineers, the azure log in process extends beyond the web portal. Command-line tools like Azure CLI and Azure PowerShell are essential for automation and scripting.
Logging In with Azure CLI
The Azure CLI is a cross-platform tool for managing Azure resources. To log in, open your terminal and run:
az login
This command opens a browser window where you complete the standard azure log in process. Once authenticated, the CLI stores your credentials securely in a local cache.
- Use
az login --tenant <tenant-id>to specify a directory - For service principals, use
az login --service-principal - Run
az account listto view accessible subscriptions
For more details, visit Azure CLI authentication documentation.
Logging In with Azure PowerShell
Azure PowerShell uses the Connect-AzAccount cmdlet to authenticate. Run the following in PowerShell:
Connect-AzAccount
You’ll be prompted to enter your credentials in a pop-up window. Like the CLI, it supports tenant-specific logins and service principal authentication.
- Use
Connect-AzAccount -Tenant <tenant-id> - For headless scripts, use service principal with certificate-based auth
- Run
Get-AzContextto verify your session
PowerShell is ideal for Windows administrators and those integrating Azure with existing automation workflows.
Azure Log In Security: Protecting Your Credentials
Every azure log in is a potential attack vector. Cybercriminals target cloud credentials through phishing, keyloggers, and social engineering. Protecting your login process is non-negotiable.
Use Strong, Unique Passwords
A strong password is your first line of defense. Avoid common patterns like “Password123” or “CompanyName2024.” Instead, use long, random phrases or a password manager to generate and store credentials.
- Minimum 12 characters
- Mix uppercase, lowercase, numbers, and symbols
- Never reuse passwords across accounts
Microsoft recommends using passphrases (e.g., “BlueCoffeeMug$Rains@2024”) for better memorability and security.
Enable Passwordless Authentication
Microsoft is pushing toward a passwordless future. Azure supports several passwordless options that eliminate the risk of stolen credentials:
- Microsoft Authenticator app (push notifications)
- Windows Hello for Business
- FIDO2 security keys (e.g., YubiKey)
- Biometric authentication on mobile devices
These methods use public-key cryptography, making them immune to phishing and replay attacks. Users simply approve a login request on their trusted device.
“Passwordless isn’t just convenient—it’s fundamentally more secure.” — Microsoft Identity Division
Learn how to set up passwordless sign-in at Microsoft’s passwordless guide.
Avoid Phishing and Fake Login Pages
Phishing remains the top method for stealing azure log in credentials. Attackers create fake login pages that mimic the real Azure portal.
Always verify the URL: https://portal.azure.com. Check for HTTPS and the correct domain. Never click login links in unsolicited emails.
- Enable anti-phishing policies in Microsoft Defender for Office 365
- Educate users on identifying suspicious emails
- Use DNS-based protection like DMARC and SPF
If you suspect a phishing attempt, report it immediately using Microsoft’s reporting tools.
Advanced Azure Log In Scenarios
As organizations grow, so do their authentication needs. Azure supports advanced scenarios like guest access, cross-tenant logins, and hybrid identities.
Guest User Access and B2B Collaboration
Azure AD B2B (Business-to-Business) allows organizations to invite external users (partners, vendors, clients) to access Azure resources securely.
Guests can log in using their own Microsoft account or work/school account. The azure log in experience is seamless, but admins retain control over permissions and access duration.
- Invite users via email in the Azure portal
- Assign least-privilege roles (e.g., Reader, Contributor)
- Set expiration dates for guest accounts
This is ideal for collaborative projects without sharing internal credentials.
Cross-Tenant Access and Multi-Directory Logins
Large enterprises often manage multiple Azure AD directories (tenants). Users may need to log in to different tenants based on their role or project.
During the azure log in process, users can switch directories using the directory switcher in the top-right corner of the portal. Admins can also configure cross-tenant access settings for shared resources.
- Use Azure Lighthouse for multi-tenant management
- Configure trust relationships between tenants
- Implement centralized logging for audit compliance
This flexibility supports complex organizational structures while maintaining security.
Hybrid Identity with Azure AD Connect
Many companies use hybrid environments—on-premises Active Directory synchronized with Azure AD via Azure AD Connect.
In this setup, users log in with the same credentials they use locally. The azure log in process can use:
- Password Hash Sync (PHS)
- Pass-through Authentication (PTA)
- Active Directory Federation Services (AD FS)
Each method has trade-offs in complexity, security, and user experience. PTA is often preferred for its balance of security and simplicity.
Learn more about hybrid identity at Microsoft’s hybrid authentication guide.
Future of Azure Log In: Trends and Innovations
The azure log in process is evolving rapidly. Microsoft continues to innovate in identity security, user experience, and zero-trust architecture.
Zero Trust and Continuous Authentication
Zero Trust assumes no user or device is trusted by default, even after login. Azure now supports continuous authentication, where risk is reassessed during a session.
If a user’s behavior changes (e.g., sudden data download), Azure can prompt for re-authentication or block access.
- Integrate with Microsoft Entra ID (formerly Azure AD)
- Use risk-based Conditional Access policies
- Monitor session activity in real time
This shift moves beyond the traditional “log in and forget” model to dynamic, context-aware security.
AI-Powered Identity Protection
Microsoft is leveraging AI to detect anomalous sign-ins. Azure AD Identity Protection uses machine learning to flag risky logins based on IP reputation, device health, and user behavior.
For example, if a user typically logs in from New York but suddenly appears in Russia, the system can block or challenge the login.
- Enable Identity Protection in the Azure portal
- Review risk detections and user risk policies
- Automate responses with Azure Logic Apps
This proactive defense is critical as attacks become more sophisticated.
Biometrics and Device Trust
The future of azure log in lies in device-centric authentication. Instead of relying solely on passwords, Azure increasingly trusts the device itself.
Windows Hello, Apple Touch ID, and Android biometrics are integrated into the login flow. When combined with device compliance policies, this creates a seamless yet secure experience.
“Your phone or laptop isn’t just a tool—it’s your digital identity.” — Microsoft Security Blog
Organizations adopting Intune and Autopilot can enforce device trust as a prerequisite for azure log in.
What is the correct URL for Azure log in?
The official URL for Azure log in is https://portal.azure.com. Always verify the domain and HTTPS to avoid phishing sites.
How do I reset my Azure password?
If you’ve forgotten your password, click “Forgot password” on the login screen. Follow the prompts to verify your identity using a recovery method like email, phone, or authenticator app. If self-service is not enabled, contact your administrator.
Can I log in to Azure without a password?
Yes. Azure supports passwordless authentication using the Microsoft Authenticator app, FIDO2 security keys, Windows Hello, or biometrics. These methods are more secure and convenient than traditional passwords.
Why am I being asked for MFA every time I log in?
If MFA prompts appear frequently, it may be due to browser settings, private mode usage, or Conditional Access policies. Enable “Remember multi-factor authentication” on trusted devices to reduce prompts. Note that this option is only available for devices marked as compliant.
What should I do if I’m locked out of my Azure account?
If locked out, wait 15–30 minutes for the lockout to expire, or use the “Forgot password” option. If you’re an admin and cannot regain access, contact Microsoft Support or use a break-glass emergency account to restore access.
Mastering the azure log in process is essential for anyone using Microsoft’s cloud platform. From basic portal access to advanced command-line tools and security best practices, understanding how to securely authenticate ensures you can work efficiently while protecting your organization’s data. By leveraging MFA, conditional access, and emerging passwordless technologies, you’re not just logging in—you’re future-proofing your identity in the cloud.
Further Reading: